Our VAPTS services provide organizations with powerful capabilities to help identify exploitable vulnerabilities in internal and external systems. Full, focused or targeted services designed to ensure organizations get the most out of their limited budget. A range of specialized assessments conducted on information systems or individual system components to identify exploitable vulnerabilities that could impact your business.
Secure your perimeter - test the networks and systems exposed to the entire Internet as a whole.
Learn MoreUncover Vulnerabilities and insecure Application functionalities - Identify security risks, including the OWASP Top 10
Learn MoreTest your network & infrastructure for weaknesses - Testing includes communications, access and interactions of a wide range of connected network devices
Learn MoreTest the effectiveness of your social engineering controls - Identify vulnerabilities relating to attacks that leverage people and process.
External Penetration testing is done to test the effectiveness of perimeter security controls, to prevent and detect attacks as well as identifying weaknesses in the organization’s network and internet-facing assets such as web, mail and FTP servers.

Get your Network and Applications assessed from an external view and understand how you can secure it.
Get custom report outlining actionable insights.
Prioritized risk identification and profiling with risk mitigation recommendations
Continuous risk mitigation with optional monthly or quarterly scans
An external network or external infrastructure penetration test aims to assess your network for vulnerabilities and security issues in servers, hosts, devices and network services. Our team of experts use the tried and proven methodologies to efficiently detect and prevent any opportunities for an external attack.
The majority of web applications today are highly functional, often channeling critical business functions and containing and processing sensitive organization data. This presents a real world opportunity for threat actors to exploit vulnerabilities within web applications for nefarious purposes.
Identify security risks, including the OWASP Top 10 – Both Web and Mobile Application Penetration tests seek to highlight any weaknesses or misconfigurations in Application configuration and functionality.

Application testing to be focused on key security mechanisms, including but not limited to the OWASP Top 10.
Custom report outlining actionable insights..
Prioritized risk identification and profiling with risk mitigation recommendations.
Additional risk reduction with optional monthly or quarterly scans.
Web application penetration tests seek to identify and address security vulnerabilities before malicious attackers discover them. The most serious web application vulnerabilities can expose highly sensitive information or provide unauthorized and unrestricted access to business resources. Multiple test types, including authenticated and API testing.
Mobile app penetration testing involves expert mobile security specialists following a rigorous methodology to determine the overall security posture of a given Mobile application. Proven expertise in securing iOS and Android applications Multiple test types, including authenticated and API testing on both iOS and Android platforms.
Testing includes communications, access and interactions of a wide range of connected network devices. A Network penetration test aims to assess the security of your network infrastructure using a variety of techniques from a number of vantage points, both external and internal. This testing includes Communication, access and interactions of a wide range of connected network devices including servers, laptops, storage drives, printers, network appliances, and even the web or mobile applications Get custom report outlining actionable insights. Prioritized risk identification and profiling with risk mitigation recommendations. Continuous risk mitigation with optional monthly or quarterly scans.
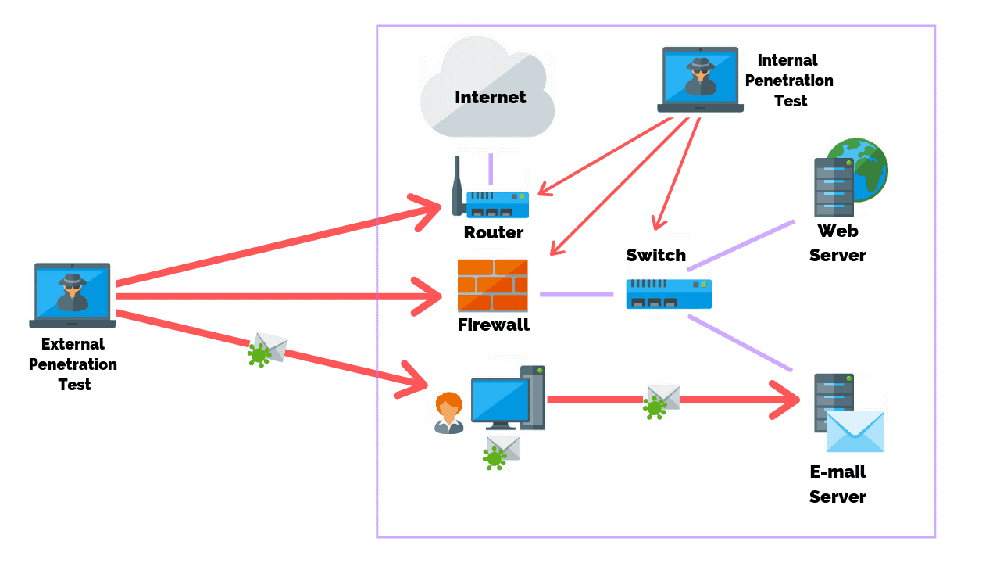
This testing includes Communication, access and interactions of a wide range of connected network devices including servers, laptops, storage drives, printers, network appliances, and even the web or mobile applications.
Get custom report outlining actionable insights.
Prioritised risk identification and profiling with risk mitigation recommendations.
Continuous risk mitigation with optional monthly or quarterly scans.
Risk mitigation advice to address vulnerabilities based on risk rating. Where resolution is not possible, we recommend alternative risk minimization options and preventive countermeasures.
Custom reports based on the industry sector and size. Includes both high level summary for management review and in-depth technical report showing proof of existence and example exploit codes. Recommendations based on industry best practices.
Test debrief call to run through the findings. We make sure you understand the critical and high severity vulnerabilities to address along with guidance on remediation and countermeasures. If required, live demonstrations of possible exploitation with guidance on how to secure the environment going forward.
Trusted service delivered by qualified and experienced security consultants, who can help you build a stronger security perimeter.
Competitive pricing with unmatched service quality to suit all business sizes.
2024 Cyinetmax | Designed by Sino Soft Limited
Social Engineering Penetration Test
A social engineering penetration test will help you evaluate your employees’ susceptibility to social engineering attacks. These tests focus on people and process, rather than on technology. The objective of a social engineering attack typically includes manipulating people into divulging confidential information or performing an activity that benefits the attacker, preferably without those people realizing. While technology is very important, it doesn’t represent the entire attack surface of a given organization.
Include social engineering tests in your Information security program and get complete assurance against real world threats.
Maximise your employees’ security vigilance.
Get assurance that includes consideration of real-world threats such as phishing.
Custom report outlining actionable insights.